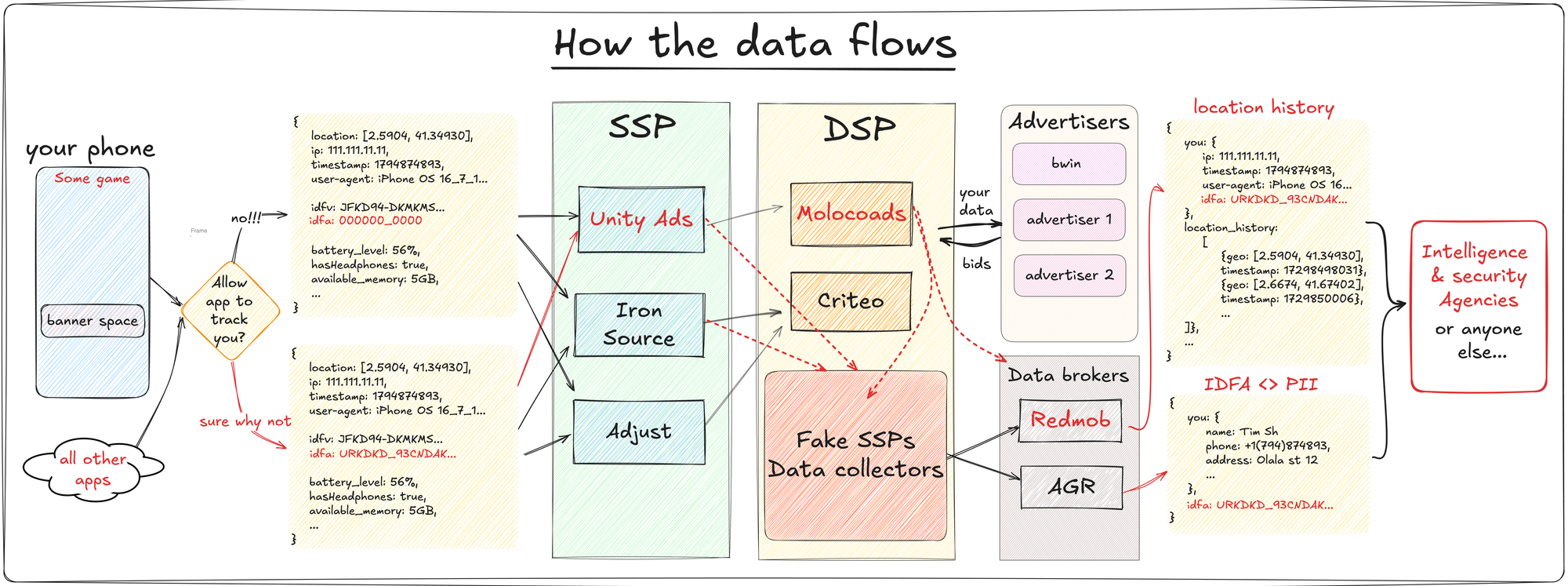
How I tracked myself down using leaked location data in the in-app ads, and what I found along the way.
Great article. It should be noted that your web browser allows websites to do this with javascript.
Also, since this tracking isn’t really trying to hide, people have compiled lists of the dns names of the destinations of these requests.
If you host a DNS server and you take that list and return NULL for everyone on the list. Then clients on your network who have ad tracking software will try to look up the destination to send your data and your DNS will tell them that there is nowhere to send the data and so the data isn’t delivered. So, all of the smart TVs, game consoles, refrigerators, toasters and doorknobs which automatically send data but you cannot configure will fail because they use DNS also.
This sounds complicated to do, but I’m just describing Pi-hole (https://pi-hole.net/). It only takes a few minutes to setup the container and change your router’s DHCP configuration in order to give out the address of the Pi-hole DNS server.
Assuming you’re on Linux, which you are because you’re a reader of a c/Privacy… right?
Am I the only person who doesn’t use apps with in-app ads?
Part of why I root is to block them using Ad-away.
I avoid them if possible and block the ads if not.
You can check an app for embedded trackers & get a list of permissions here:
Very interesting, but also scary.
Switch to grapheneos NOW
No OS gonna protect you from apps spying you. The solution is to not use the said apps.
Google Play services likely does this too, so to actually protect yourself from this spyware you will need to use either microG or containerized Google Play services like how GrapheneOS has implemented.
Not everyone has a pixel.
Everyone will have a next phone though.
Bad Android apps with ads: you’re the product mate.